Hoy toca una entrada de las que me ha costado más de elaborar.
Tengo bastantes routers cisco en los clientes y la mayoría de vpn’s (más de 50), las tengo con ipsec over GRE y EIGRP…. de esta manera, todas las sedes se ven entre ellas y no me tengo que preocupar de las rutas.
La idea, es montar routers mikrotik virtuales y aprovechar el espacio, ahorrar corriente, etc..
El escenario que propongo es sencillo:
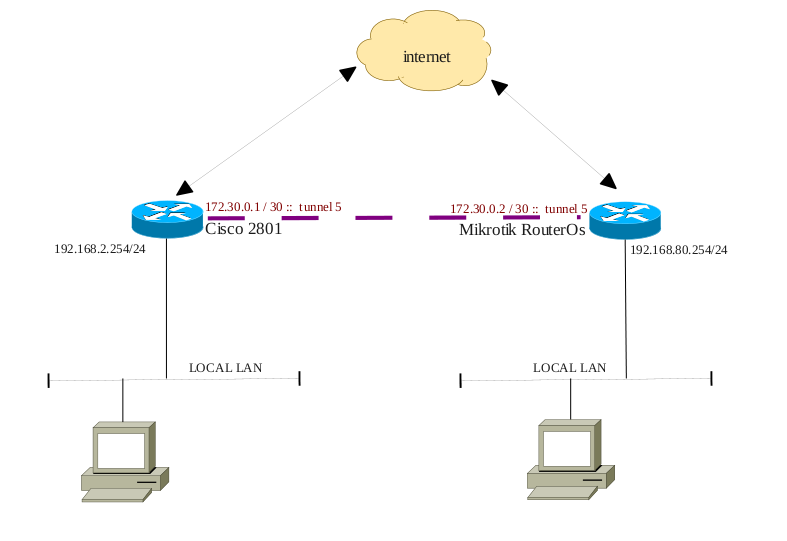
Tenemos en un lado, la red local: 192.168.80.0/24 y en el otro extremo, la red 192.168.2.0/24.
La red que usaremos para el tunel, será: 172.30.0.0/30.
Empezamos con la configuración del router cisco:
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
lifetime 3600
crypto isakmp key superClave address 1.1.1.1 no-xauth
crypto ipsec transform-set trans_3des esp-3des esp-md5-hmac
mode transport
!
crypto ipsec profile mikro
set transform-set trans_3des
Colocaremos ipsec en modo transporte para no perder la información de routing, entre otras cosas y nos creamos un profile para el tunel con la mikrotik.
Creamos en Tunel GRE:
interface Tunnel5
description CONNECTED TO oficina mikrtik
ip address 172.30.0.1 255.255.255.252
ip mtu 1476
tunnel source FastEthernet0/0
tunnel destination 1.1.1.1
tunnel protection ipsec profile mikro
Y configuramos OSPF, con las áreas:
router ospf 10
log-adjacency-changes
redistribute static subnets
network 192.168.2.0 0.0.0.255 area 0
network 172.30.0.0 0.0.0.3 area 0
Y por último, la ruta estática (de momento no me funciona de otra manera), con la red remota:
cisco(conf-if)# ip route 192.168.80.0 255.255.255.0 tunnel 5
Y ahora vamos por la mikrotik:
/interface ethernet
/interface gre
add disabled=no dscp=0 l2mtu=65535 local-address=1.1.1.1 mtu=1476
name=tunnel5 remote-address=2.2.2.2
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha1 disabled=no enc-algorithms=3des
lifetime=30m name=default pfs-group=modp1024
add auth-algorithms=md5 disabled=no enc-algorithms=3des lifetime=59m59s name=
cisco pfs-group=none
/routing ospf instance
set [ find default=yes ] disabled=no distribute-default=never in-filter=
ospf-in metric-bgp=auto metric-connected=20 metric-default=1
metric-other-ospf=auto metric-rip=20 metric-static=20 name=default
out-filter=ospf-out redistribute-bgp=no redistribute-connected=as-type-1
redistribute-other-ospf=as-type-1 redistribute-rip=no
redistribute-static=as-type-1 router-id=0.0.0.0
/routing ospf area
set [ find default=yes ] area-id=0.0.0.0 disabled=no instance=default name=
backbone type=default
add area-id=192.168.80.0 disabled=no instance=default name=area11 type=
default
/routing ospf-v3 instance
set [ find default=yes ] disabled=no distribute-default=never metric-bgp=auto
metric-connected=20 metric-default=1 metric-other-ospf=auto metric-rip=20
metric-static=20 name=default redistribute-bgp=no redistribute-connected=
no redistribute-other-ospf=no redistribute-rip=no redistribute-static=no
router-id=0.0.0.0
/ip address
add address=192.168.80.254/24 comment="added by setup" disabled=no interface=
ether1_lan network=192.168.80.0
add address=1.1.1.1/32 disabled=no interface=public_interface network=
1.1.1.1
add address=172.30.0.2/30 disabled=no interface=tunnel5 network=172.30.0.0
/ip dhcp-server config
set store-leases-disk=5m
/ip ipsec peer
add address=2.2.2.2/32 auth-method=pre-shared-key comment=
"tunel IPSEC pruebas angel" dh-group=modp1024 disabled=no dpd-interval=2m
dpd-maximum-failures=5 enc-algorithm=3des exchange-mode=main
generate-policy=no hash-algorithm=md5 lifebytes=0 lifetime=1d
my-id-user-fqdn="" nat-traversal=no port=500 proposal-check=obey secret=
superClave send-initial-contact=yes
/ip ipsec policy
add action=encrypt disabled=no dst-address=2.2.2.2/32 dst-port=any
ipsec-protocols=esp level=require priority=0 proposal=cisco protocol=47
sa-dst-address=2.2.2.2 sa-src-address=1.1.1.1 src-address=
1.1.1.1/32 src-port=any tunnel=no
/ip neighbor discovery
set ether1_lan disabled=no
set public_interface disabled=no
set tunnel5 disabled=yes
/ip route
add comment="added by setup" disabled=no distance=1 dst-address=0.0.0.0/0
gateway=1.1.1.2 scope=30 target-scope=10
/routing filter
add action=accept chain=ospf-out disabled=no distance=1 invert-match=no
prefix=192.168.80.0/24 protocol=connect,ospf set-bgp-prepend-path=""
/routing igmp-proxy
set query-interval=2m5s query-response-interval=10s quick-leave=no
/routing mme
set bidirectional-timeout=2 gateway-class=none gateway-keepalive=1m
gateway-selection=no-gateway origination-interval=5s preferred-gateway=
0.0.0.0 timeout=1m ttl=50
/routing ospf area range
add advertise=yes area=area11 cost=calculated disabled=no range=
192.168.80.0/24
/routing ospf interface
add authentication=none authentication-key="" authentication-key-id=1 cost=10
dead-interval=40s disabled=no hello-interval=10s instance-id=0 interface=
all network-type=broadcast passive=no priority=1 retransmit-interval=5s
transmit-delay=1s use-bfd=no
add authentication=none authentication-key="" authentication-key-id=1 cost=10
dead-interval=40s disabled=no hello-interval=10s instance-id=0 interface=
public_interface network-type=broadcast passive=yes priority=1
retransmit-interval=5s transmit-delay=1s use-bfd=no
/routing ospf network
add area=backbone comment="local lan" disabled=no network=192.168.80.0/24
add area=backbone comment="tunnel 5 network" disabled=no network=
172.30.0.0/30
/system clock
set time-zone-name=Europe/Madrid
/system clock manual
set dst-delta=+00:00 dst-end="jan/01/1970 00:00:00" dst-start=
"jan/01/1970 00:00:00" time-zone=+00:00
set name=cpd_router
/system lcd
set contrast=0 enabled=no port=parallel type=24x4
set enabled=yes mode=unicast primary-ntp=130.206.3.166 secondary-ntp=
130.206.3.166
/system ntp server
set broadcast=no broadcast-addresses="" enabled=no manycast=yes multicast=no
jueves, febrero 26, 2026
la configuracion de los router esta entendible, creo que la veo asi debido a que conozco de CISCO, pero respecto a MK no se donde defines IPSEC donde el tunnel gre, veo que haces varias configuraciones, cual seria le necesaria para lo planteado
Pues en las etiquetas:
/ip ipsec proposal
/ip ipsec peer
add address=2.2.2.2/32 auth-method=pre-shared-key comment=
“tunel IPSEC pruebas angel†dh-group=modp1024 disabled=no dpd-interval=2m
dpd-maximum-failures=5 enc-algorithm=3des exchange-mode=main
generate-policy=no hash-algorithm=md5 lifebytes=0 lifetime=1d
my-id-user-fqdn=※ nat-traversal=no port=500 proposal-check=obey secret=
superClave send-initial-contact=yes
/ip ipsec policy
add action=encrypt disabled=no dst-address=2.2.2.2/32 dst-port=any
ipsec-protocols=esp level=require priority=0 proposal=cisco protocol=47
sa-dst-address=2.2.2.2 sa-src-address=1.1.1.1 src-address=
1.1.1.1/32 src-port=any tunnel=no
aquà tienes fase 1 y fase 2